Cybersecurity

Arrests in Tap-to-Pay Scheme Powered by Phishing
Authorities in at least two U. states last week independently announced arrests of Chinese nationals accused of perpetrating a novel form of tap-to-pay fraud using mobile devices. Details released by authorities so far indicate the mobile wallets being used by the scammers were created through online phishing scams, and that the accused were relying on a custom Android app to relay tap-to-pay transactions from mobile devices located in China. Authorities in Knoxville, Tennessee last week said they arrested 11 Chinese nationals accused of buying tens of thousands of dollars worth of gift cards at local retailers with mobile wallets created through online phishing scams. The Knox County Sheriff’s office said the arrests are considered the first in the nation for a new type of tap-to-pay fraud. Responding to questions about what makes this scheme so remarkable, Knox County said that while it appears the fraudsters are simply buying gift cards, in fact they are using multiple transactions to purchase various gift cards and are plying their scam from state to state. “These offenders have been traveling nationwide, using stolen credit card information to purchase gift cards and launder funds,” Knox County Chief Deputy Bernie Lyon wrote. “During Monday’s operation, we recovered gift cards valued at over $23,000, all bought with unsuspecting victims’ information. ” Asked for specifics about the mobile devices seized from the suspects, Lyon said “tap-to-pay fraud involves a group utilizing Android phones to conduct Apple Pay transactions utilizing stolen or compromised credit/debit card information,” [emphasis added]. Lyon declined to offer additional specifics about the mechanics of the scam, citing an ongoing investigation.
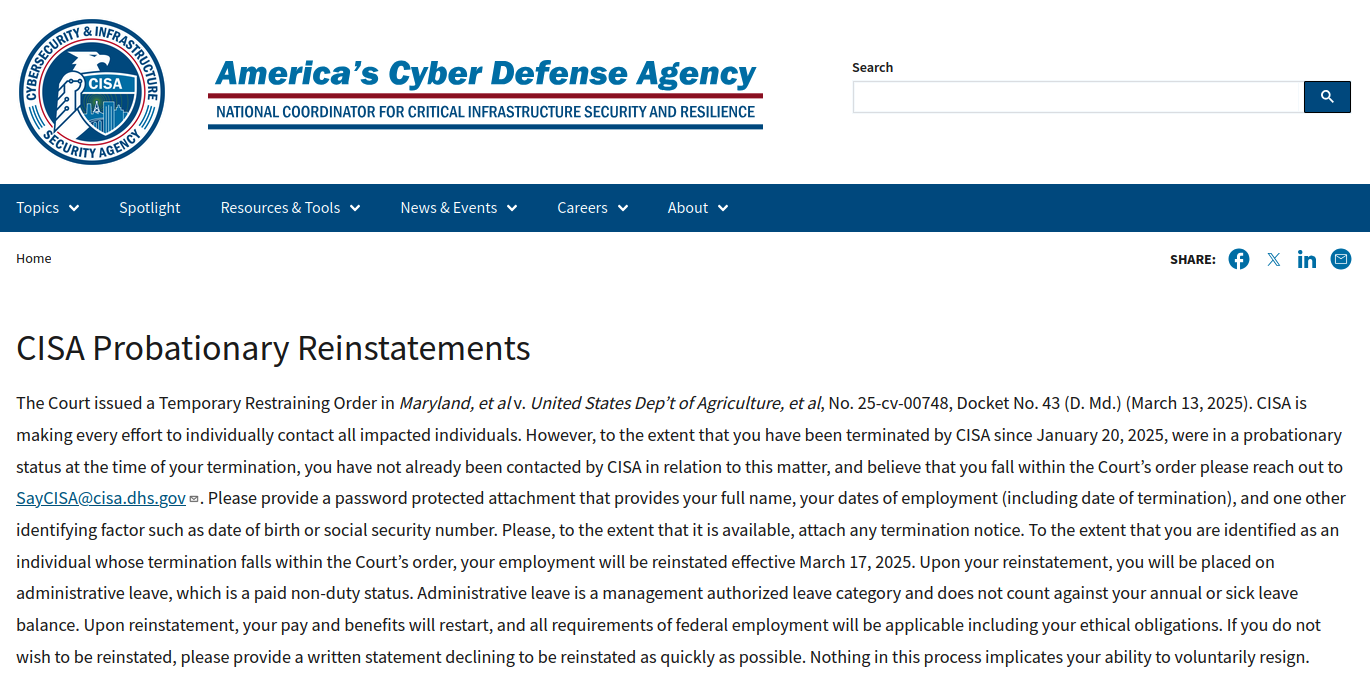
DOGE to Fired CISA Staff: Email Us Your Personal Data
A message posted on Monday to the homepage of the U. Cybersecurity & Infrastructure Security Agency (CISA) is the latest exhibit in the Trump administration’s continued disregard for basic cybersecurity protections. The message instructed recently-fired CISA employees to get in touch so they can be rehired and then immediately placed on leave, asking employees to send their Social Security number or date of birth in a password-protected email attachment — presumably with the password needed to view the file included in the body of the email. The homepage of cisa. gov as it appeared on Monday and Tuesday afternoon. On March 13, a Maryland district court judge ordered the Trump administration to reinstate more than 130 probationary CISA employees who were fired last month. On Monday, the administration announced that those dismissed employees would be reinstated but placed on paid administrative leave. They are among nearly 25,000 fired federal workers who are in the process of being rehired. A notice covering the CISA homepage said the administration is making every effort to contact those who were unlawfully fired in mid-February. “Please provide a password protected attachment that provides your full name, your dates of employment (including date of termination), and one other identifying factor such as date of birth or social security number,” the message reads.